🚨 Immediate Action Required
On September 12, 2025, the FBI issued FLASH alert FLASH-20250912-001 warning about two cybercriminal groups actively targeting Salesforce platforms. Major companies including Google, Chanel, Qantas, and Allianz have already been compromised. Your organization could be next.
The Threat Landscape Has Changed
In 2025, cybercriminals have evolved beyond traditional network breaches. They’re now targeting the very features that make Salesforce powerful—its integrations and ease of use. Two sophisticated threat groups, UNC6040 and UNC6395, have developed methods that bypass traditional security controls including MFA, making them extremely dangerous.
What makes these attacks so concerning:
- They use legitimate authentication mechanisms (OAuth tokens)
- They bypass MFA and login monitoring
- The activity appears to come from trusted integrations
- No vulnerabilities in Salesforce itself are exploited
- They target the human element through sophisticated social engineering
How These Attacks Work
Attack Flow Diagram
Visual representation of both attack methods targeting Salesforce environments
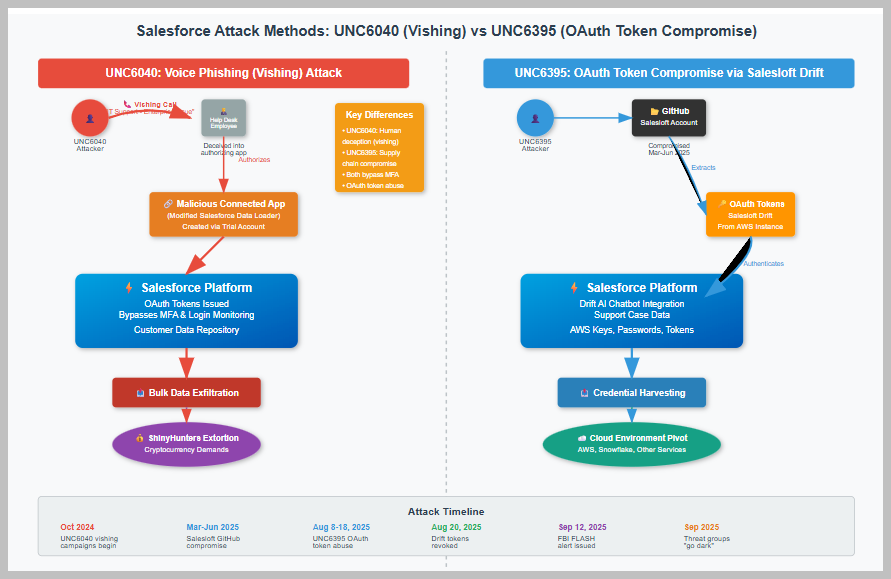
The diagram shows the complete attack flow from initial contact to data exfiltration
🎯 UNC6040: Voice Phishing (Vishing)
- Initial Contact: Attackers call help desk posing as IT support
- Social Engineering: Claim to resolve “enterprise-wide connectivity issues”
- Deception: Guide employees to authorize malicious connected apps
- Persistence: Modified Salesforce Data Loader grants ongoing access
- Exfiltration: Bulk data extraction via API queries
- Extortion: ShinyHunters demands cryptocurrency payments
🔗 UNC6395: OAuth Token Compromise
- Supply Chain Attack: Compromise Salesloft’s GitHub (March-June 2025)
- Token Theft: Extract OAuth tokens from AWS Drift instance
- Direct Access: Use stolen tokens to authenticate to Salesforce
- Data Mining: Target support cases for credentials and tokens
- Lateral Movement: Use harvested credentials to access other cloud services
- Scale Impact: Pivot to multiple cloud environments
FBI Indicators of Compromise
The FBI has released specific technical indicators to help organizations detect these attacks:
🔍 Key IOCs to Monitor:
- Suspicious User-Agent Strings: “Salesforce-Multi-Org-Fetcher/1.0”, “python-requests/2.32.4”
- Malicious URLs: login.salesforce.com/setup/connect with suspicious user codes
- IP Addresses: Over 70 known malicious IPs in the FBI alert
- Unusual API Activity: Bulk data queries from connected apps
- New OAuth Apps: Especially modified Data Loader applications
How to be Proactive and Prevent these Issues in the Future
Comprehensive approach to protecting your Salesforce environment
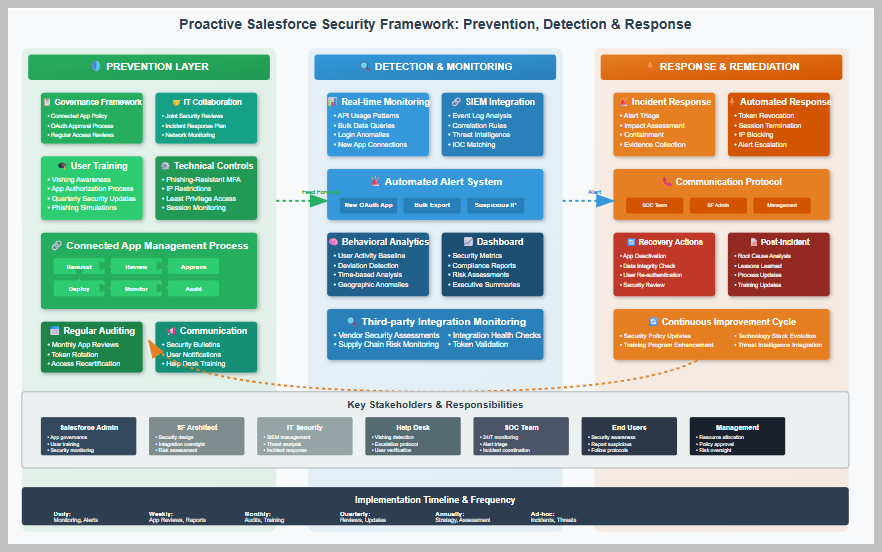
Shows the complete security lifecycle from prevention through response
🛡️ Prevention Layer
- Connected app governance framework
- Comprehensive user training programs
- Phishing-resistant MFA implementation
- Regular security audits and reviews
🔍 Detection Layer
- Real-time API monitoring
- SIEM integration and correlation
- Behavioral analytics
- Automated alert systems
⚡ Response Layer
- Incident response procedures
- Automated containment actions
- Communication protocols
- Post-incident improvements
🎯 Bottom Line Up Front (BLUF)
- Immediate Action: Audit all connected apps in your Salesforce org TODAY
- Train Your Team: Help desk staff are the first line of defense against vishing
- Monitor API Activity: Implement real-time monitoring for bulk data queries
- Review OAuth Tokens: Rotate and validate all third-party integration tokens
- Establish Governance: Require approval for all new connected apps
Implementation Roadmap
Week 1: Immediate Actions
- Audit all connected apps using our checklist
- Review help desk training procedures
- Implement FBI IOC monitoring
- Establish incident response team
Week 2-4: Foundation Building
- Deploy enhanced API monitoring
- Conduct user training sessions
- Implement governance processes
- Test incident response procedures
Month 2-3: Optimization
- Fine-tune monitoring rules
- Conduct security assessments
- Expand training programs
- Establish regular review cycles
Don’t Wait for an Attack
The threat actors behind these campaigns are sophisticated, well-funded, and actively targeting organizations like yours. The FBI’s alert is not just a warning—it’s a call to action.
📞 Need Help Implementing These Measures?
Our team of Salesforce security experts can help you assess your current security posture and implement these recommendations. Please feel free to email me at buyan@eigenx.com for any questions
Please subscribe
Subscribe to our mailing list and get tips to maximize salesforce to your email inbox.
I am honored to have your subscription. Stay tuned for tips to maximize your salesforce investment
Something went wrong.